Authored by James Rushmore via Racket News,
In March 2023, the University of Washington’s Center for an Informed Public (CIP) put out an article asserting that the Election Integrity Partnership (EIP) — comprised of the CIP, the Stanford Internet Observatory (SIO), Graphika, and the Atlantic Council’s Digital Forensic Research Lab (DFRLab) — was not a “government cut-out” controlled by the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA).
Racket has sent out numerous Freedom of Information (FOIA) requests about the Election Integrity Partnership. Recently, we received several new batches of results from the University of Washington that cast doubt on their earlier assertions. These disclosures, which have been added to the Racket FOIA Library, hint at a dynamic perhaps more intimate than reported. This is the first of a series of disclosures we’ll be publishing this week.
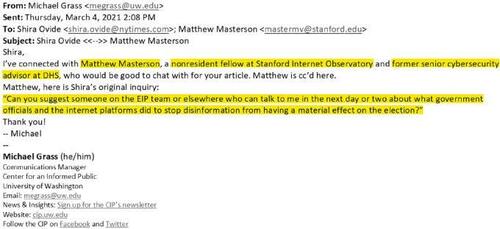
On March 4, 2021, Shira Ovide of The New York Times emailed the EIP to ask what government officials and social media platforms did to “stop disinformation from having a material effect on the [2020] election.”
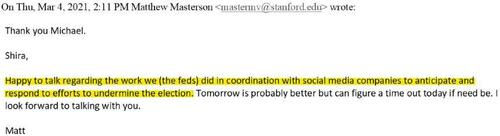
The response came from Matthew Masterson, at the time a non-resident policy fellow at the Stanford Internet Observatory. Masterson then only just finished working as a senior cybersecurity advisor at CISA, a position he held from March 2018 to December 2020. He stayed at CISA through the 2020 election, then moved to Stanford just in time to receive Ovide’s inquiry as a private citizen. His response is humorous in its frankness (emphasis ours):
Happy to talk regarding the work we (the feds) did in coordination with social media companies to anticipate and respond to efforts to undermine the election.
Masterson’s choice of verb is interesting. For years, “anti-disinformation” activists have insisted that state actors merely contacted social media companies with helpful tips regarding troublesome accounts. Masterson’s response suggests CISA was in close contact with platforms like Twitter throughout the 2020 election cycle, though Ovide wasn’t told how close. (See the accompanying article by Matt Taibbi to learn more.) He’s explicit in his characterization of the EIP-CISA dynamic as a coordinated effort.
When reached for comment, Ovide directed Racket to an article she published shortly after her conversation with Masterson. The former DHS official told Ovide that “coordination was the biggest change that helped shore up digital defenses in [2020] election management systems.” At the time, Masterson said, “This is as good [sic] as the federal government has worked on any issue in my experience.” The piece doesn’t mention the EIP, but it still captures the degree to which federal law enforcement agencies like CISA were in contact with 2020 election officials.
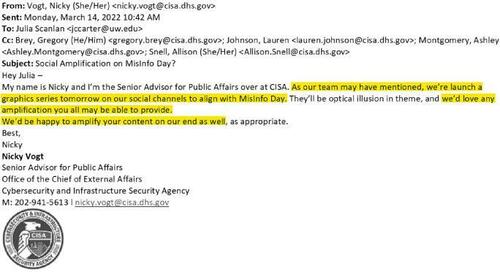
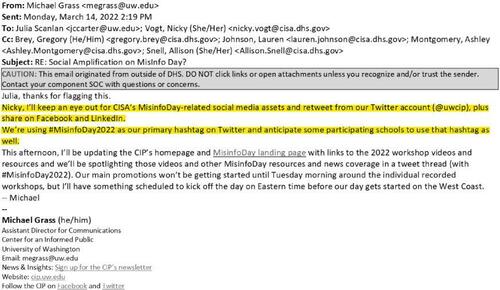
You’ll find more evidence of the tight-knit relationship between CISA and the EIP in their communications the following year. On March 14, 2022, Nicky Vogt, the senior advisor for public affairs at CISA, reached out to the EIP in order to coordinate their messaging efforts on MisinfoDay. (MisinfoDay, for those unfamiliar, is an annual celebration intended to help students, educators, and librarians “learn how to navigate complex information environments and make informed decisions about what to believe online.”)
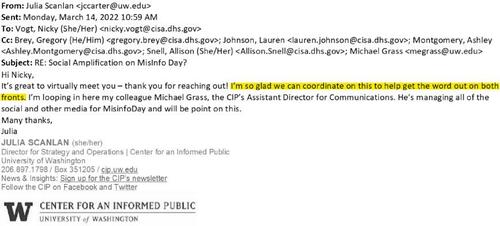
In an email marked with the subject line “Social Amplification on MisInfo Day?”, Vogt asked Julia Carter Scanlan, the CIP’s director for strategy and operations, if the EIP could “amplify” CISA’s MisinfoDay-themed graphics on its social media accounts. Vogt offered to return the favor by promoting the EIP’s MisinfoDay content on CISA’s accounts. Also worth noting is the “as our team may have mentioned” at the start of Vogt’s email. CISA and the EIP seemed to be on very friendly terms!
Carter Scanlan’s response was enthusiastic (emphasis ours):
I’m so glad we can coordinate on this to help get the word out on both fronts. I’m looping in here my colleague Michael Grass, the CIP’s Assistant Director for Communications. He’s managing all of the social and other media for MisinfoDay and will be point on this.
The word of the day is “coordination.”
A few hours later, Vogt made contact with Grass, who promised to share the EIP’s MisinfoDay content on the CIP’s Twitter, Facebook, and LinkedIn accounts. Grass also indicated that other schools would be participating in the day’s festivities through the #MisinfoDay2022 hashtag.
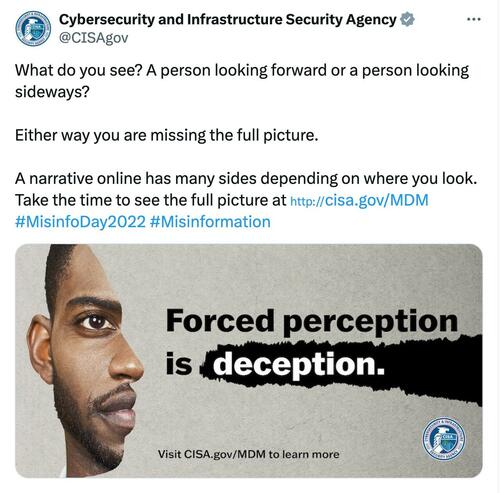
Here’s the tweet CISA asked Grass to promote.
These emails illustrate the synergies between the “anti-disinformation” industry and the national security state. In theory, the two factions are supposed to be separate entities, but in practice, they represent the same interests. It’s not often that a single disclosure offers evidence of the alacrity with which outfits like the EIP did the bidding of federal law enforcement agencies. We should be grateful for their candor.
Below are a few more excerpts from this latest batch of FOIA disclosures, which you can access in full at the Racket FOIA Library.
-
In July 2020, shortly before the EIP officially launched, the key players debated what they wanted to call their partnership. Emerson Brooking of the Atlantic Council recommended against going with the “Election Disinformation Partnership,” arguing that it could “very easily be made to sound like [they] are spreading disinformation,” and suggested the “2020 Partnership.” His suggestion was co-signed by the SIO’s Alex Stamos (“[S]ounds a bit like an Olympics thing.”) and Graphika’s Camille François (“It will fit on a shirt”). The group ultimately settled on the “Election Integrity Partnership,” a name that Stamos described as generic and unlikely to be misinterpreted. (See page 109.)
-
On November 17, 2021, Ashley Quarcoo, a senior director at the Partnership for American Democracy, reached out to the EIP to discuss how they could take steps to prepare for “election misinformation” in the 2022 cycle. (See pages 47 and 48.)
-
On October 31, 2022, Mark Scott of Politico emailed the SIO’s Renée DiResta with some examples of Telegram channels that were spreading “election-related falsehoods” in swing states during the runup to the midterm elections. Scott asked DiResta if she could account for the spread of such theories “from fringe networks like Telegram to more mainstream networks.” (See page 17.)
Click here to access Racket’s library of University of Washington FOIA productions.
Subscribe to Racket News here...
Authored by James Rushmore via Racket News,
In March 2023, the University of Washington’s Center for an Informed Public (CIP) put out an article asserting that the Election Integrity Partnership (EIP) — comprised of the CIP, the Stanford Internet Observatory (SIO), Graphika, and the Atlantic Council’s Digital Forensic Research Lab (DFRLab) — was not a “government cut-out” controlled by the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA).
Racket has sent out numerous Freedom of Information (FOIA) requests about the Election Integrity Partnership. Recently, we received several new batches of results from the University of Washington that cast doubt on their earlier assertions. These disclosures, which have been added to the Racket FOIA Library, hint at a dynamic perhaps more intimate than reported. This is the first of a series of disclosures we’ll be publishing this week.
On March 4, 2021, Shira Ovide of The New York Times emailed the EIP to ask what government officials and social media platforms did to “stop disinformation from having a material effect on the [2020] election.”
The response came from Matthew Masterson, at the time a non-resident policy fellow at the Stanford Internet Observatory. Masterson then only just finished working as a senior cybersecurity advisor at CISA, a position he held from March 2018 to December 2020. He stayed at CISA through the 2020 election, then moved to Stanford just in time to receive Ovide’s inquiry as a private citizen. His response is humorous in its frankness (emphasis ours):
Happy to talk regarding the work we (the feds) did in coordination with social media companies to anticipate and respond to efforts to undermine the election.
Masterson’s choice of verb is interesting. For years, “anti-disinformation” activists have insisted that state actors merely contacted social media companies with helpful tips regarding troublesome accounts. Masterson’s response suggests CISA was in close contact with platforms like Twitter throughout the 2020 election cycle, though Ovide wasn’t told how close. (See the accompanying article by Matt Taibbi to learn more.) He’s explicit in his characterization of the EIP-CISA dynamic as a coordinated effort.
When reached for comment, Ovide directed Racket to an article she published shortly after her conversation with Masterson. The former DHS official told Ovide that “coordination was the biggest change that helped shore up digital defenses in [2020] election management systems.” At the time, Masterson said, “This is as good [sic] as the federal government has worked on any issue in my experience.” The piece doesn’t mention the EIP, but it still captures the degree to which federal law enforcement agencies like CISA were in contact with 2020 election officials.
You’ll find more evidence of the tight-knit relationship between CISA and the EIP in their communications the following year. On March 14, 2022, Nicky Vogt, the senior advisor for public affairs at CISA, reached out to the EIP in order to coordinate their messaging efforts on MisinfoDay. (MisinfoDay, for those unfamiliar, is an annual celebration intended to help students, educators, and librarians “learn how to navigate complex information environments and make informed decisions about what to believe online.”)
In an email marked with the subject line “Social Amplification on MisInfo Day?”, Vogt asked Julia Carter Scanlan, the CIP’s director for strategy and operations, if the EIP could “amplify” CISA’s MisinfoDay-themed graphics on its social media accounts. Vogt offered to return the favor by promoting the EIP’s MisinfoDay content on CISA’s accounts. Also worth noting is the “as our team may have mentioned” at the start of Vogt’s email. CISA and the EIP seemed to be on very friendly terms!
Carter Scanlan’s response was enthusiastic (emphasis ours):
I’m so glad we can coordinate on this to help get the word out on both fronts. I’m looping in here my colleague Michael Grass, the CIP’s Assistant Director for Communications. He’s managing all of the social and other media for MisinfoDay and will be point on this.
The word of the day is “coordination.”
A few hours later, Vogt made contact with Grass, who promised to share the EIP’s MisinfoDay content on the CIP’s Twitter, Facebook, and LinkedIn accounts. Grass also indicated that other schools would be participating in the day’s festivities through the #MisinfoDay2022 hashtag.
Here’s the tweet CISA asked Grass to promote.
These emails illustrate the synergies between the “anti-disinformation” industry and the national security state. In theory, the two factions are supposed to be separate entities, but in practice, they represent the same interests. It’s not often that a single disclosure offers evidence of the alacrity with which outfits like the EIP did the bidding of federal law enforcement agencies. We should be grateful for their candor.
Below are a few more excerpts from this latest batch of FOIA disclosures, which you can access in full at the Racket FOIA Library.
-
In July 2020, shortly before the EIP officially launched, the key players debated what they wanted to call their partnership. Emerson Brooking of the Atlantic Council recommended against going with the “Election Disinformation Partnership,” arguing that it could “very easily be made to sound like [they] are spreading disinformation,” and suggested the “2020 Partnership.” His suggestion was co-signed by the SIO’s Alex Stamos (“[S]ounds a bit like an Olympics thing.”) and Graphika’s Camille François (“It will fit on a shirt”). The group ultimately settled on the “Election Integrity Partnership,” a name that Stamos described as generic and unlikely to be misinterpreted. (See page 109.)
-
On November 17, 2021, Ashley Quarcoo, a senior director at the Partnership for American Democracy, reached out to the EIP to discuss how they could take steps to prepare for “election misinformation” in the 2022 cycle. (See pages 47 and 48.)
-
On October 31, 2022, Mark Scott of Politico emailed the SIO’s Renée DiResta with some examples of Telegram channels that were spreading “election-related falsehoods” in swing states during the runup to the midterm elections. Scott asked DiResta if she could account for the spread of such theories “from fringe networks like Telegram to more mainstream networks.” (See page 17.)
Click here to access Racket’s library of University of Washington FOIA productions.
Subscribe to Racket News here…
Loading…